

In recent years, with the widespread application of Secure Multi-Party Computation (MPC), Threshold Homomorphic Encryption (ThFHE), and Multi-Key Homomorphic Encryption (MKFHE) in data privacy protection and distributed computing, there has been an increasing demand for solutions that do not rely on trusted third parties. However, many of these protocols require public parameters generated by third parties during the initialization stage, introducing potential security risks. Thus, ensuring the leakage resilience of encryption systems in a trust-free setting has become a key issue.
Recently, the Center for Automated Reasoning and Cognition at our institute presented a research paper titled "Lattice-Based More General Anti-leakage Model and Its Application in Decentralization" at the 29th Australian Conference on Information Security. This paper introduces a generalized anti-leakage model based on Euclidean lattices, quantifying the average conditional min-entropy H∞ (s|sA + e)of the private key s after the attacker adaptively selects the matrix A. Compared to traditional models, this new model offers a more accurate description of information leakage scenarios in protocols.
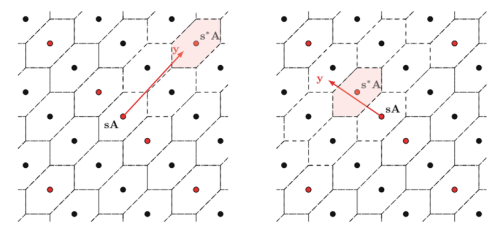
Figure 1: Closest lattice point to y. The red point is in set S. The left panel shows the closest point to y being on S, while the right panel illustrates that the closest point is not on S.
Building on this model, the research team optimized the existing MKFHE schemes by replacing traditional Dual-GSW schemes with GSW-type ciphertexts, significantly reducing key and ciphertext length; improving communication efficiency during key generation, reducing the system's computational complexity and interaction overhead; and supporting private keys and noise with different distributions (e.g., discrete Gaussian distributions) to ensure robustness across various application scenarios.
This research provides a more efficient and secure solution for multi-party computation in decentralized settings, laying a theoretical foundation for the development of leakage-resilient encryption systems that do not depend on third parties.
**Link to the paper**: https://link.springer.com/chapter/10.1007/978-981-97-5028-3_3
Xiaokang Dai, a Ph.D. student at Chongqing Research Institute, is the first author of the paper, and researcher Wenyuan Wu is the corresponding author. The research was supported by key projects from the Ministry of Science and Technology and the Western Young Scholars Program of the Chinese Academy of Sciences.